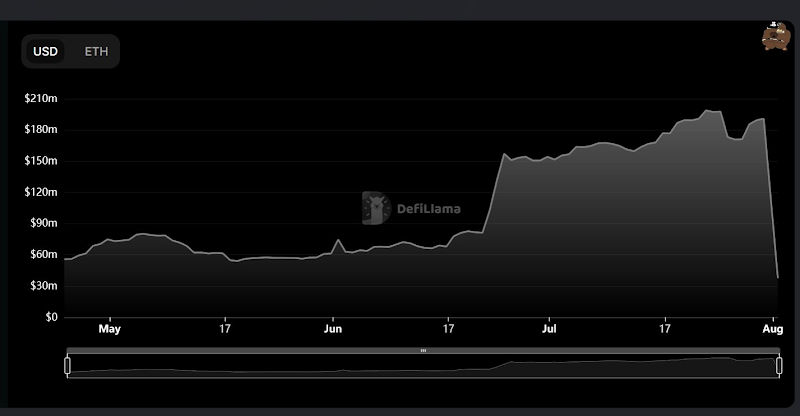
According to CertiK Alert, the cross-chain bridge Nomand Bridge has been hacked on this Monday, with losses over $190 million. The Nomand team soon acknowledged this exploit and stated that “we are currently looking into the incident and will provide updates when they have them.”

What Happened Exactly?
Usually, a cross-chain bridge works by “wrapping” tokens in a smart contract and then issuing native assets users can use on another chain. If the smart contract gets exploited, the wrapped tokens would lose backing and become worthless, and this is where Nomand Bridge went wrong.
The Nomad team recently made an update to one of its smart contracts, which made it easy for users to spoof transactions. This means users were able to withdraw money that did not belong to them from Nomand Bridge.
Unlike previous cross-chain bridge attacks – Ronin ($624m), Wormhole($326m), Harmony($100m), QBridge($80m) where there may be a single culprit behind the looting, the Nomad attack is rather chaotic. Due to its loophole in smart contract, all it takes is to “find a transaction that worked, find/replace the other person’s address with yours, and then re-broadcast it.”
A Deeper Dive into Nomad’s Cross-Bridge Design
The Nomad team could have avoided this attack. However, early this year in February, they stated that they gave up light clients in Nomad’s design because of technical difficulties of implementing light clients. This means that they would forgo security in exchange of lower operating costs and simplicity. And now that decision costs them $190 million.

If they had implemented Light Client in the first place, this attack could possibly be avoided, as Light Client is the only decentralized cross-chain technology with 100% security. Nomad’s tragedy is another wake-up call for those who favor simplicity over security.
Developing and deploying the Light Client is not a “light” task. As the industry leading omichain infrastructure builder, MAP invested full-stack development effort with over 20 experienced engineers for almost four years, and finally it will go live at the end of this month. MAP Protocol chooses Light Client in the beginning and we keep our nose to the grindstone to make it happen. Cross-chain security is the heart and soul of MAP Protocol.
Of course, the loophole in Nomad’s smart contract is to blame for this attack. Essentially, any service provider should thoroughly audit its services before it goes alive. As in our case, we conduct triple code test cases, hashed timelock, and engaged third-party professional auditors like Certik for extra assurance.
How Nomad Can Restore its Security and Confidence
For restoring security and confidence, Nomad team really should consider to go back to Light Client technology. MAP Protocol highly welcomes Nomad to replace their current solution and rebuild on MAP’s infrastructure built upon Light Client technology. We will support Nomad in all technical aspect possible regarding light-client implementation. Smart contract management will also be another key piece for restoring security. It would be helpful if they follow more strict security practices – conduct triple code test cases, add hashed timelock every time before they go live, and engage more professional auditors.